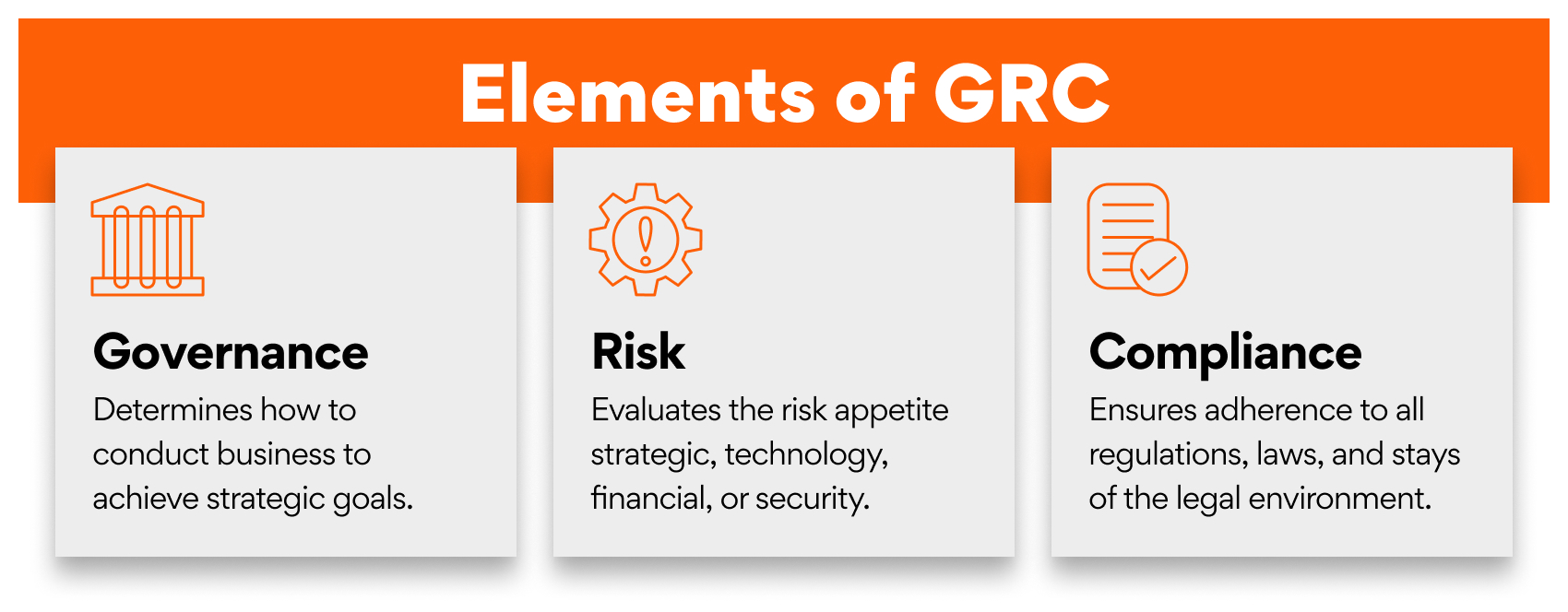
GRC – short for governance, risk, and compliance – has existed for nearly two decades. Every modern business has had to onboard elements of GRC to ensure business continuity and revenue growth while taking controlled risks necessary for maintaining a competitive edge.
Why Prioritize GRC Now
Unprincipled misconduct, mistakes, and miscalculations have cost enterprises more than $1 trillion annually, especially when technology dynamics, customer expectations, and market shifts require enterprises to act fast to tap into the first-mover advantage. Strategic decision-making requires multi-dimensional data to understand how much risk an enterprise can comfortably onboard, what new compliance and legal liabilities the enterprise will expose itself to, and what changes it would need to bring in the way it operates to do all of this sustainably.
Here’s why a GRC strategy is the most important ingredient in any business decision where data is involved:
- Technology Hype: The pace of technology change has outpaced the speed at which enterprises can respond, requiring them to make bold calls without diving deep into the implications and impact of onboarding a new technology. Artificial Intelligence (AI) makes a fitting case – it has always been ahead of enterprises ability to manage it, requiring a hurried catch-up that leads to very close hits and misses before it delivers the intended business benefits. The story continues with Generative AI (GenAI), where the hype around productivity gains completely blindsided the discourse on data used for model training, hallucinations, or biases. The rush to adopt AI and its forms has given way to AI Washing, where enterprises make tall claims of using AI in innovative ways but do not. The US Security and Exchange Commission charged two investment advisors $400,000 in civil penalties for making false and misleading claims about their purported use of AI.
- Security Implications: As enterprises move data and applications outside of on-premises data centers to cloud-first shared infrastructure, enable more remote workers, and allow endpoints not directly controlled by security teams access to their network – they open up touchpoints that bad actors could exploit. Data breaches come with a cost – $4.45 million for fixing one in 2023, a 15% increase over three years. Beyond the financial cost, a security incident creates a trust deficit among customers and investors, damaging reputations and taking years to reverse.
- Tightening Regulatory Scrutiny: Across industries, increasing regulatory oversight creates the need to weigh in business decisions and operations against risks arising out of non-compliance. In 2023, penalties levied by the US regulators on financial firms rose by 69% year-on-year to $5 billion. Regulators globally prioritize data security and privacy, mandating enterprises to set up protocols and mechanisms to safeguard customer data against all known vulnerabilities and report breaches within a stipulated time. Tech giants such as Amazon, Instagram, TikTok, and T-Mobile have cumulatively shelled out billions of dollars as non-compliance penalties since 2021.
Getting Started with a GRC Strategy
Creating a robust GRC strategy is not a one-time event. This requires regular stakeholder cadences where they assess the change in the business environment and map its impact on operations. The pitfalls come at the time of follow-ups and when executing the changes in the GRC strategy. A technology partner with a strong governance and risk portfolio can help enterprises define, implement, and monitor the integrated risk and compliance framework to mature the organization’s risk and compliance posture.
Here’s how:
- Requirement Analysis
- Design and Implement Enterprise GRC Platform
- Design and Development of Reports
- Data Object Model and Data Structures
- Data Validation, Conversion, and Migration
- Functional and Performance Testing
The Persistent Edge
Persistent offers a curated GRC automation service that is integrated into the business context and offers a comprehensive view of enterprise security, risk, and compliance posture. We deliver:
- Enhanced Risk Management: With our business-integrated and proactive risk management
- Improved Decision-Making: Clearer governance and compliance criteria, with a 360-degree view of security risk and compliance posture
- Improved Regulatory Compliance: Adherence to industry standards and regulations with a dive deep into evolving regulations and best practices for compliance
- Operational Efficiency: Increased performance and process optimization with automation
With our deep understanding of the business domain and our security expertise, we help our clients bridge the gap between business and IT to manage risks, create a specialized GRC strategy and design, an integrated a holistic view of risk and compliance posture backed by proactive and vigilant risk monitoring. Our global clients bank on us to confidently navigate the complex and evolving business risk landscape, while staying abreast with new developments in regulations and threat vectors to anticipate and prepare for potential headwinds.
To know how Persistent can help your organization develop and execute a bespoke GRC strategy, click here.
Author’s Profile
William Eliah (Willie)
Senior Practitioner, Data Security Practice, Data Protection, GRC





