The days of dedicated Offshore Delivery Centers (ODCs) have given way to geographically distributed teams collaborating on a project from their homes via constantly moving devices. Although the pandemic only accelerated the shift, the death of the ODCs has been underway ever since cloud adoption picked up. As businesses pivot to digital, the centralized IT environments break down into shared infrastructure, and on-premises datacenter-hosted applications are moved to cloud-hosted or Software-as-a-Service (SaaS) platforms – to be accessed from anywhere, anytime.
But not by anyone. That is the chink in the armor of a burgeoning IT network that needed to provide dynamic connectivity and access to users outside the confines of traditional network configurations. Security became a top concern as enterprise traffic slowly shifted away from on-premises data centers to the cloud, with increasing edges (or devices) vying for access.
Networking systems overlaid with point security solutions as check posts failed to orchestrate access securely. The lack of collaboration on these two fronts leads to blind spots that are difficult to manage and secure, opening vulnerabilities.
As per “The Cloud Data Security Imperative,” 39% of organizations have suffered the loss of cloud-resident sensitive data, and an additional 20% suspect they have, but can’t be certain. Of the organizations that have suffered or suspected they have suffered cloud data loss events, 42% indicated SaaS applications were the target. More than a third (38%) ranked SaaS applications as the primary target for hackers, closely followed by cloud-based storage (36%).
Enter SASE: Converging Network & Security for SaaS Applications
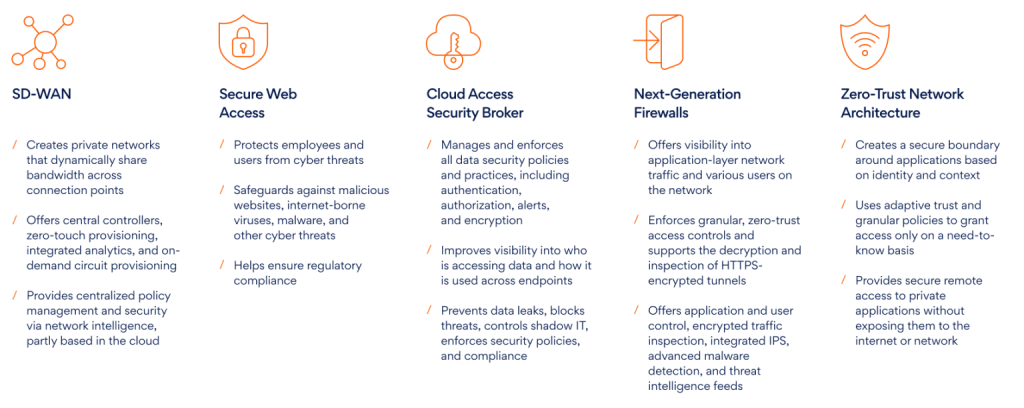
Introduced by Gartner in 2019, the term Secure Access Service Edge or SASE refers to an emerging offering combining comprehensive network capabilities with comprehensive security functions to support digital enterprises’ dynamic, secure access needs. By marrying networking functions with cybersecurity approaches, SASE brings security to the heart of the network, making it secure by default. This means access to SaaS applications is contextual, rule–based, and policy–compliant – no matter where the access requests originate from or where the application is hosted. It has several security components working to ensure the overall security posture remains robust – and only verified users have access to information or applications.
How SASE helps enterprises manage network access and security mandates
- More Control and Visibility: Real-time management of who is accessing what applications and from where with a centralized console.
- Better network performance and reliability: Keeps a tab on bandwidth utilization and orchestrates traffic securely to keep things flowing at the required speed.
- Less complexity: With integrated security solutions, there is no need to ship, install, and upgrade hardware at remote/branch locations. Security kicks in simply by connecting to the Internet.
- Mobility: Offers the same security levels regardless of where the user is – the office, home, airport, or café, making users and organizations less reliant on backhauling traffic to the data center.
- Seamless User Experience: As users connect directly to the app and not the network, it is all transparent connectivity for the user. A smoother experience for both SaaS or Cloud-hosted applications and on-premises applications.
- Greater agility: By utilizing an internet connection instead of a fully individualized configuration, you can expand your business to new locations more easily and efficiently.
- Reducing costs: SASE allows enterprises to integrate different solutions to fortify the security posture, instead of maintaining separate tool or solution stacks that work in silos.
- Complete visibility across hybrid environments: See everything going on in your environments – users, apps, data – under your watchful eye.
- Monitoring and reporting: Enterprises often deploy multiple networking and security solutions, making it unmanageable to deal with individual incidents that could add to noise. With SASE, enterprises get a single view of all their networking and security tools that make it easier to track metrics, generate reports, and monitor access controls.
Leading Defense Supplier Prepares for a Hybrid Workforce by Securing 93% of Web Traffic
Persistent assisted a major manufacturer of defense supplies in upgrading its IT security architecture and gaining better control over user access to data and internal applications. Persistent significantly reduced the client’s attack perimeter by implementing identity-based, contextualized, and application-specific access policies. We leveraged Zscaler Private Access (ZPA) to strengthen the client’s security posture, ensuring secure access to resources regardless of the user’s location, device, or network. The client secured 93% of their web traffic with advanced threat and malware protection, enabling a modern hybrid workplace with a seamless and secure user experience.
As a managed security service provider, Persistent offers comprehensive network security services to reduce network threats and maximize uptime. We have developed infrastructure security solutions that align with the ‘Identify, Defend, Protect, and Respond’ framework, enabling enterprises to detect and combat network threats with defense-in-depth mechanisms swiftly.
Our team of security experts leverages a thriving ecosystem of security solution partners to design, deploy, configure, integrate, and manage network protection controls to align security operations with IT strategy and minimize impact on business. We prepare enterprises to ward off evolving cybersecurity threats and reduce the visible impact of malicious activity.
Connect with us to secure enterprise assets and data with Persistent’s proactive approach.
Author’s Profile
Tushar Errum
Technical Support Lead, Security Practice







