Gaps in the current cybersecurity landscape
Cybersecurity threats are ever more sophisticated and challenging to combat. Victims of ransomware attacks have shelled out $449.1 million in the first six months of this year. For all of 2022, that number did not even reach $500 million. New ways to breach network defenses, such as supply chain attacks, zero-day exploits, fileless malware, advanced persistent threats (APT) and ransomware-as-a-service, now circumvent traditional cybersecurity gates for unauthorized access to sensitive data and systems. These techniques actively evade detection and outdo current antivirus software that is effective only against known threats and relies primarily on signature-based detection methods. With the proliferation of mobile devices used by remote or hybrid employees, the threat landscape expands beyond organization-controlled endpoints such as desktops, laptops, servers, etc.
Why EDR is the game changer for IT security
Irrespective of who owns the endpoints, they must be continuously analyzed to preempt potential threats and security breaches. EDR brings behavioral analytics, machine learning, threat intelligence, and rapid incident response capabilities to actively detect and block known/unknown threats.
There is momentum building up, with the global EDR market forecasted to grow 22.3% by the end of this decade to $18.3 billion. It offers:
- Advanced Threat Detection: Based on behavioral patterns and anomalous activities, advanced threats like zero-day exploits and fileless malware can be detected and halted by EDR solutions.
- Real-time Incident Response: Upon detecting a potential threat, immediate response actions can be initiated by EDR. These actions include isolating the affected endpoint, terminating malicious processes, or quarantining suspicious files, all of which minimize the attack’s impact.
- Endpoint Visibility: By furnishing security teams with insights into endpoint activities, teams can conduct comprehensive investigations and forensic analysis in the event of security incidents.
- Threat-Hunting Capabilities: By enabling security analysts to actively search for threats and indicators of compromise, EDR facilitates proactive defense against ever-evolving cyber threats.
- Compliance and Reporting: Detailed reports on security incidents and response actions provided by EDR solutions can aid organizations in fulfilling regulatory compliance mandates.
- Centralized management: Centralized management of EDR solutions facilitates organization-wide deployment and administration, simplifying the task for security teams.
- Reporting and analytics: The reporting and analytics capabilities that often accompany EDR solutions assist security teams in monitoring threats and enhancing the overall security stance.
- Integration with other security solutions: A holistic security approach integrates EDR solutions with various security counterparts, such as Security Information and Event Management (SIEM), Extended Detection and Response (XDR), and Security Orchestration, Automation, and Response (SOAR) for enhanced visibility, analysis, and response capabilities spanning endpoints, workloads, users, and networks.
Three factors to consider before adopting an EDR solution:
EDR is a specialized field that requires out-of-the-box thinking and hard-to-find niche skills to strategize and plan security frameworks that keep ahead of the bad actors. These three factors can provide directional guidance to security decision-makers:
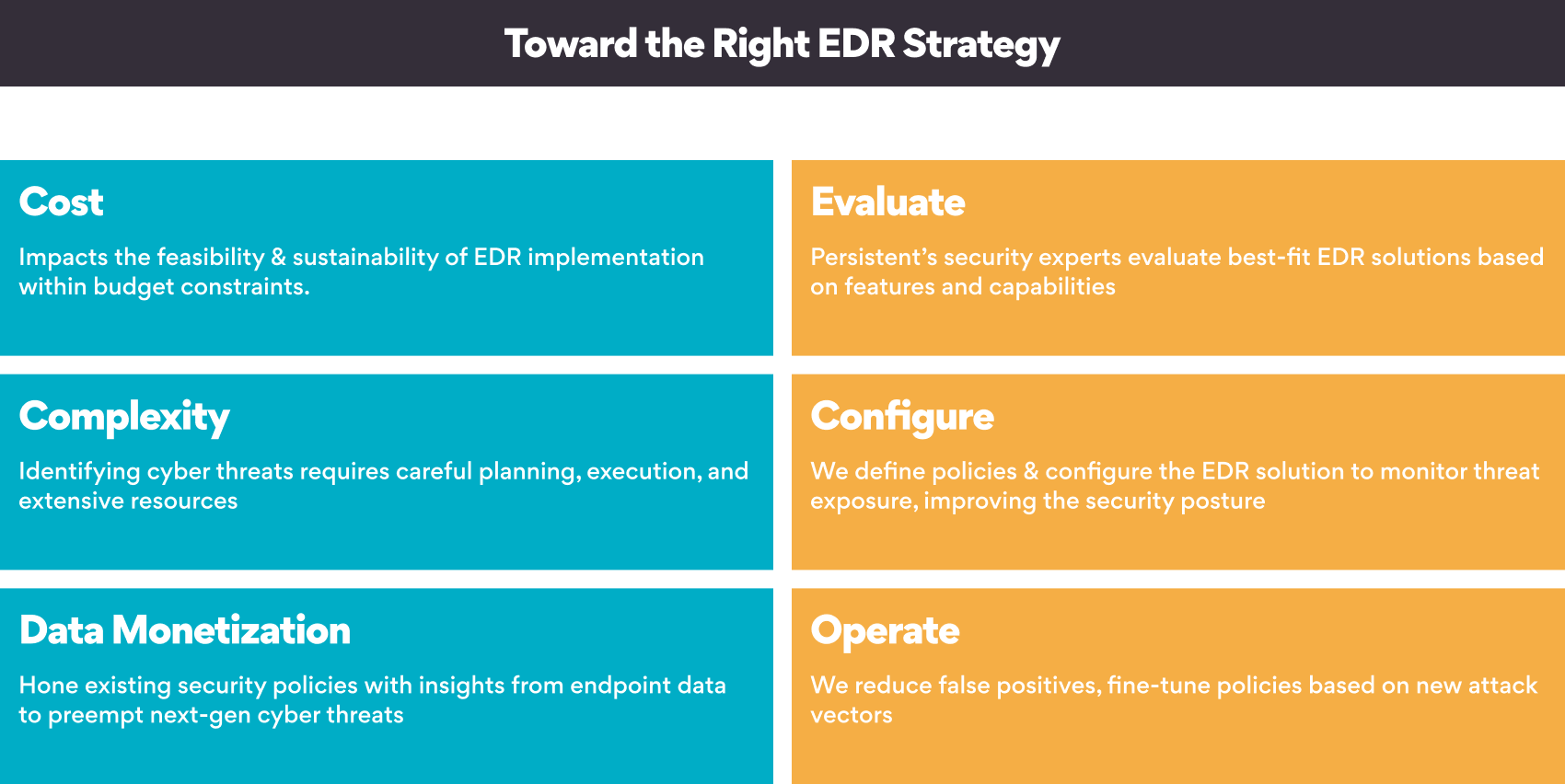
- Cost: The cost of EDR solutions can vary significantly. Teams should run a comparative analysis of the required features and capabilities of different EDR solutions before deciding.
- Complexity: EDR solutions can be complex to deploy and manage. It is important to have a team of security experts who can deploy and manage the EDR solution to achieve intended objectives.
- Data Monetization: EDR solutions generate high volumes of data, and it is crucial to have a strategy for storing and analyzing this data that can feed into and fine-tune future security endeavors.
Strengthening Endpoint Security with Persistent.
Even as a non-negotiable, EDR can be a burden and usurp critical resources and bandwidth, diluting the focus on innovation and core business activities. Persistent’s Security Architecture and Technology Consulting provides the expertise to strategize, implement, and manage EDR solutions.
We adopt a 360-degree approach to EDR that covers:
- Evaluation: Mapping and analyzing the current security landscape with the correct EDR solution.
- Implementation: Configuring EDR solutions with the right policy based on different parameters such as OS (operating systems), system type, and exposure type.
- Operations: Managed support with effective monitoring and analysis to reduce false positive alerts, fine-tuning policies based on new attack vectors, monitoring, and reporting as per client requirements with different options like 24×7 || 16×5 || 8×5.
- Threat Detection and Hunting: Threat hunting service covering remediation guidelines with skilled and experienced resources. We perform root cause analysis on an endpoint for any blocked threat or important artifact.
Start your EDR journey today with Persistent. Get in touch with us here.






